You thought companies using your cookies to advertise to you was bad? Just read these documents from Wikileaks and you might start going outside more…
Since Donald Trump was sworn in as our forty fifth president, there has been a significant spike in sales of George Orwell’s dystopian novel Nineteen Eighty-Four. A lot of this has been blamed on paranoia and has often been called an overreaction. But now there’s evidence (or more evidence) that far more aspects of Orwell’s novel are coming true than just doublespeak and thoughtcrime.
 Image VIA
Image VIA
According to a series of documents, which have been posted on the non-profit site Wikileaks, the CIA has been monitoring routers and examining internet histories for the last ten years.
Whoever is reading this, I’ll give you a chance to delete a few things before you continue.
All done? Good. As I was saying:
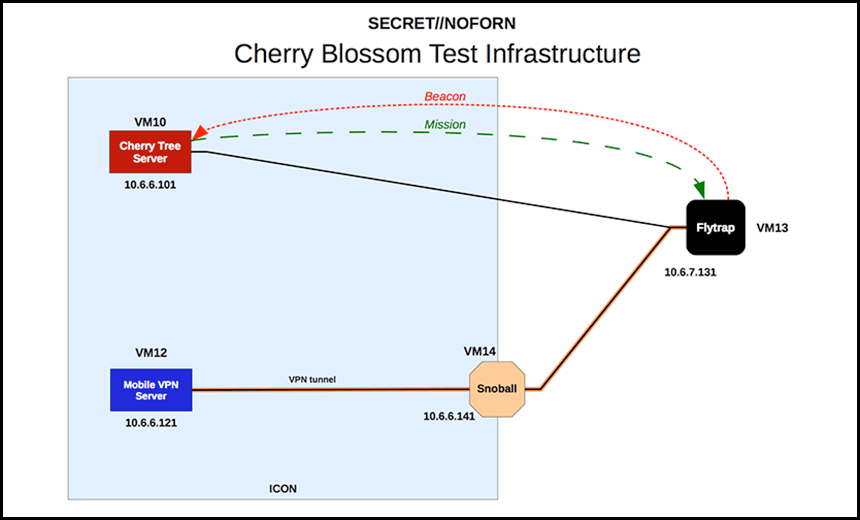
The firmware, known as the Cherry Blossom System, is used to run on home internet routers and send information about what it finds back to a system called ‘CherryTree’ for — what I hope are — surveillance reasons. They are programmed to run on routers from ten American companies including Linksys and Belkin.
The CIA has been using this technology for the last ten years to monitor people from a list of “targets of interest” (and once this article gets published, there’s a good chance I’ll be on that list as well… so if this is my last article, it’s been fun).
As one of the Wikileaks documents states: “The Cherry Blossom (CB) system provides a means of monitoring the internet activity of and performing software exploits on targets of interest.”
So what exactly happens to the targets of interest who are caught with incriminating search histories? My guess is they’re taken to Room 101, but that’s just a guess. They could be blacklisted or possibly taken to court, based on the severity of the offense, but once thing is certain… if anyone wasn’t already clearing their histories than they will now.
If the government wanted to hack us, they should’ve just called this British teenager who successfully hacked Kim-Jong Un’s account on the social media site Starcon.
Featured Image Via